We recently published an Insights piece “The Golden Scale: Bling Libra and the Evolving Extortion Economy,” which primarily focused on the Salesforce data theft extortion activity. This was associated with the cybercriminal syndicate known as Scattered LAPSUS$ Hunters. Since early October 2025, we have observed several notable developments within a Telegram channel (SLSH 6.0 part 3) used by the threat actors. This activity may provide a glimpse into how the group plans to operate in the foreseeable future. We’re providing these insights so that organizations can better prepare for and defend against this evolving threat activity.
Fallout From the Extortion Deadline
As noted in our previous Insights piece, Scattered LAPSUS$ Hunters listed the deadline for impacted organizations to make a ransom payment as 11:59 PM ET on Oct. 10, 2025. Since that time, news reports have indicated that the threat actors have leaked stolen data allegedly belonging to six companies. These companies operate across the aviation, energy and retail sectors. The leaked data allegedly includes various types of personally identifiable information (PII) such as names, dates of birth, email addresses, phone numbers and frequent flyer numbers.
Unit 42 recently tried to access the data leak site (DLS) associated with the threat actors, and noticed the website had what appeared to be a defacement message posted (see Figure 1). As a result, we were unable to determine if any victim data was still listed.

On Oct. 11, 2025, a day after the posted deadline and the release of data for the six organizations referenced above, the threat actors stated that “nothing else will be leaked.” The meaning of “the things we have cannot be leaked for obvious reasons” is unclear (see Figure 2). These “obvious reasons” could mean increased attention and action from law enforcement due to who owns the data or its type.
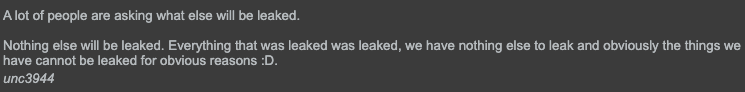
As shown below in Figure 3, the threat actors appear to potentially be stepping away from any activities until the beginning of next year. A post after this one states “I promise you, you WILL feel our wrath.”
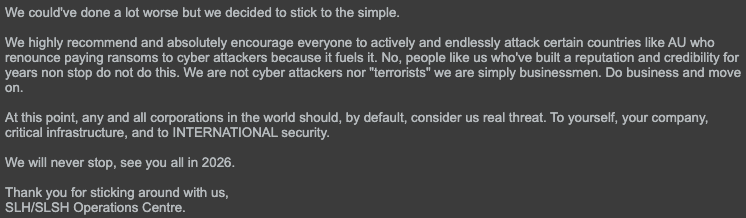
Extortion-as-a-Service Program Advertisement
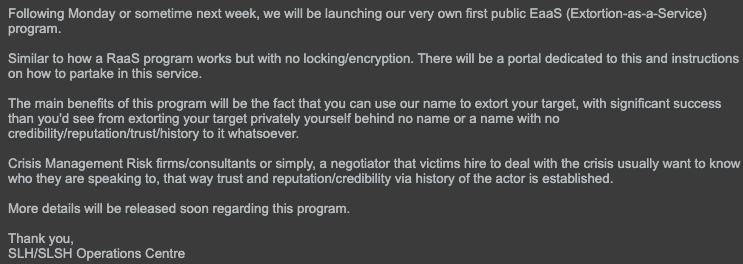
On Oct. 10, 2025, shortly prior to their self-imposed deadline, the threat actors formally alluded to the launch of their extortion-as-a-service (EaaS) program as shown in Figure 4. They claim this EaaS program will be similar to a typical ransomware-as-a-service (RaaS) program with a clear difference: no file encryption. As noted in my previous Insights piece, one likely factor for this shift is to potentially fly under the radar of law enforcement attention. This could be motivated by their focus on disrupting ransomware operations in recent years.
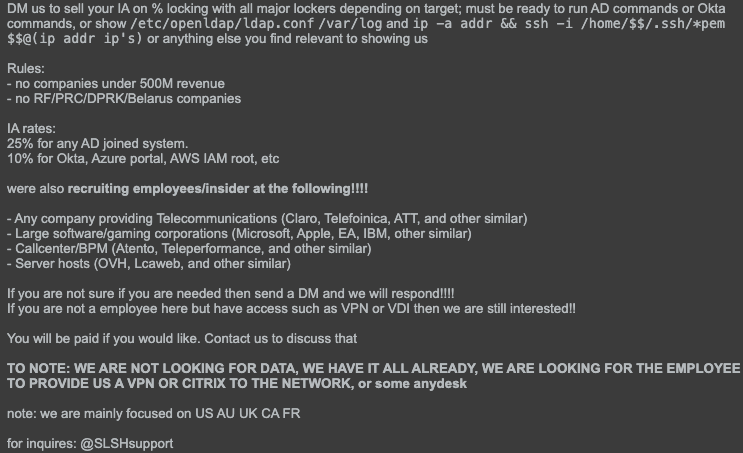
Renewed Insider Access Recruitment
On Oct. 5, 2025, the threat actors posted an advertisement seeking insider access at organizations across a variety of industries, as seen in Figure 5.
As also noted by ReliaQuest on their X account, the threat actors state their primary interest is in acquiring access to call centers, gaming companies, hosting providers, software-as-a-service (SaaS) and telecom organizations. These organizations would be based in countries such as the U.S., UK, Australia, Canada and France.
Threat actors affiliated with “The Com” have previously advertised interest in partnering with insiders at targets of interest to them. This was reported in our May 2025 update on Muddled Libra (aka Scattered Spider).
Potential Emergence of New Ransomware
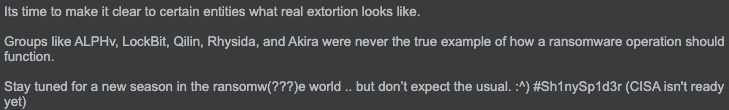
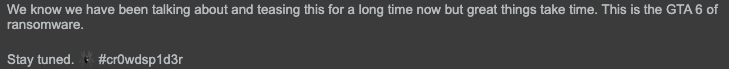
On Oct. 4, 2025, the threat actors claimed to be developing a new form of ransomware named “SHINYSP1D3R” as noted in Figures 6 and 7. These posts appear to be related to observations previously noted by Falconfeeds in August 2025. It is currently unclear if the aforementioned ransomware is still under development or simply a false claim.
What Comes Next — and What I Recommend You Do
Given that the clearnet version of Scattered LAPSUS$ Hunters’ newly launched DLS is unavailable at this time, it is unclear if any of the victims listed on the site made a ransom payment to the threat actors.
Additionally, it remains relatively uncertain if the EaaS program advertised by the threat actors will be as lucrative of a business model as they likely hoped it would be. Given that the advertisement specifically cites the removal of any file encryption in comparison to a traditional RaaS program, organizations may be less willing to make a ransom payment considering the potential lack of operational disruption.
Finally, it is not evident why the threat actors would potentially be interested in operating both an EaaS and a RaaS program, other than attempting to diversify their revenue streams. This is certainly something Unit 42 will continue to monitor going forward.
As noted in our previous Insights piece, the theft and leakage of PII, including loyalty program details (e.g., frequent flyer numbers) from some victim organizations (specifically those in hospitality) could enable cybercriminals to conduct identity theft and other types of fraud, including fueling the growth of fraudulent travel agencies advertised across underground cybercrime forums and Telegram channels.
Given the rise of RaaS programs in recent years, many organizations have developed incident response playbooks specifically to prepare for a ransomware event in terms of operational disruption. I believe it is now time for organizations to create similar playbooks for the growing threat of EaaS programs, specifically to prepare for the reputational risks associated with such events. This should include having third-party experts on standby via retainer to assist with potential negotiations, verification of stolen data and other related actions.
If your organization has been threatened with data theft extortion by Scattered Lapsus$ Hunters or other cybercriminals, the Unit 42 Incident Response team is here and ready to support with either a suspected compromise or to reduce the risk via a proactive threat assessment.








